Andrew Hodgkinson found a workaround for the latest Firefox hickups. Mozilla removed the non-standard two-parameter eval( statement, scope ) function which was used by the Firefox add-ons that implement identity selection through Information Cards. SUN's java problems that the openinfocard id selector experiences continue to bug us. With Firefox 3 the openinfocard selector is really usable only for managed cards because the java part of the selector is mainly used to issue self-issued tokens. Managed cards are handled by javascript code.
You can download the latest version of the openinfocard selector from the project's repository.
I still recommend to use Firefox 2 until SUN and Mozilla fix the java problems.
Tuesday, September 30, 2008
openinfocard for Firefox >= 3.0.2
Posted by
Unknown
at
3:29 PM
0
comments
![]()
Labels: firefox3, id selector, information card, openinfocard
Friday, September 26, 2008
Bugzilla@Mozilla – Bug 457068
The number of bugs in Firefox and the Firefox Java plugin that affect the openinfocard id selector increased in the last days/weeks. Not funny.
- eval(..., scope) regression
- javascript instanceof not working with Java classes
- AccessControlException for java based Firefox extensions
- javascript array constructor not working with Java classes
- window.java is sometimes defined but sometimes not
Sun says they can not fix the java plugin for java 6 update 10...
Aaargh.
Maybe it is time to build Information Card support into Firefox and other Mozilla applications directly?! This is worth a post on its own.
Posted by
Unknown
at
10:43 PM
0
comments
![]()
Labels: extension, firefox, java, javascript, mozilla, openinfocard
Certified Secure Software Lifecycle Professional
"(ISC)2 launched a brand new certification program designed to validate secure software development practices and expertise and address the increasing number of application vulnerabilities."
I hope that the future CSSLP knows that software needs external authentication.
Pamela was preaching this to us at DIDW2008 and it is true.
When a company plans to buy software then we need requirements for external authentication in the request for proposal. This is a must!
And the software should understand claims because "Claims Change Everything!".
External authentication gives you more security because you can choose an established authentication software for authentication in contrast to having to rely on a home-grown authentication module by a database vendor or search engine maker.
Says Axel Nennker, CISSP, CISA, Security Preacher
Posted by
Unknown
at
9:45 PM
0
comments
![]()
Labels: claims, information card
Thursday, September 25, 2008
Firefox 3.0.2 breaks ID Selector Browser Add-Ons
The current update of Firefox to version 3.0.2 breaks the Firefox ID selector browser add-ons. This does affect the openinfocard and the CardSpace4Firefox selector. I have not tried it but I assume that the other Firefox add-ons (Bandit/DigitalMe) are broken too. Thank you Mozilla (again).
I guess that eval( statement, doc ) stopped working. In the end the capturing of form-submit-events and the html-object-value-getter do not work due to this.
I am trying to fix this ASAP.
Posted by
Unknown
at
7:56 AM
0
comments
![]()
Labels: bug, CardSpace4Firefox, firefox3, mozilla, openinfocard
Wednesday, September 24, 2008
Drag & Drop Login
On Monday I published a version of the openinfocard identity selector that allows drag & drop selection of information cards at a relyingparty.
While this is NON-standard I would like it if some relying parties would jump onto this train. And of course I hope that this or something like it will become Standard.
Some thoughts about this:
Why: It is cool. You want to drag a card onto the relyingparty.
What is the problem with the current standard? The object tag has no width and height. Although the object-element was originally intended by the W3C to handle media data like video, flash, pdf, etc this was/is not the way the object tag is intended to be used by ISIP and the ISIP Web Guide as defined by Microsoft. Here the object-element provides information about the required and optional claim, the token type etc but it does not occupy space on the web page. This means that there is nothing you can drop a card onto.
Solution: Introduce a parameter to the object-element that signifies the HTML element where a card can be dropped on. The identity selector then adds drag&drop handlers to this HTML-element and these handlers trigger the identity selector when a cardId is dropped on the HTML-element with the right icDropTargetId.
This is a 1-to-1 relationship between object-element and droptarget-element.
The drop target is inside a form that gets submitted when a cardId is dropped.
Technical detail: The thing that is dragged has the mime-type "application/x-informationcard-id". If you are a card selector outside of Firefox then all you need to do to participate in this is to create a drag-"thingy" with this mime-type. The openinfocard id selector will accept only things dropped onto the drop-target with this mime-type. Easy, isn't it?!
There is of course room for improvement. We could aggree on dragging a whole card of mime-type "application/x-informationcard" and compare the tokentype and supported claimtype before accepting the dragged card...
Compability with CardSpace: The icardie.dll does not care if there are extra parameters for the object-element. Your relyingparty works with CardSpace when this new parameters is present. There is just no drag&drop feature.
Posted by
Unknown
at
11:30 AM
2
comments
![]()
Labels: CardSpace, drag and drop, openifnocard
Monday, September 22, 2008
Drop into a Site
I just uploaded a new verion of the XMLDAP RP source code and a new version of the openinfocard card selector.
You still have to compile you own version of the XMLDAP relyingparty because the current server still lacks a valid cert.
Signature validation of an newly imported card seems to fail too everytime. Sorry. Working on that (too).
Now for the new stuff. You can now display a list of your Firefox Identity Selector's cards in the browsers sidebar by pressing Ctrl-Shift-I. When you then drag a card onto the Information Card Icon the identity selector gets started and you can select a card to generate a token for the relyingparty. Cool.
It would be even cooler if the dragged card was preselected but for this I have to change the interface between browser add-on and identity selector.
The current interface for the getBrowserToken function is:
GetBrowserToken: function (
issuer , recipientURL, requiredClaims, optionalClaims , tokenType,
privacyPolicy, privacyPolicyVersion, serverCert, issuerPolicy);
I will just add the new parameter cardid to this call. And while I am at it I will introduce a new parameter sslMode. "sslMode" tells the selector whether the browser thinks that the serverCert is an extended validation certificate or not. Adding more and more parameters to the call does not seem optimal but the xpt interface in mozilla code only allows simple and some more types. I can not define structs/records etc. Theses changes to the API affect the other Firefox extension too. I have to change CardSpace for Firefox too. And maybe others will make use of this API too? (Another subproject I don't have time for: convert the DigitalMe/Bandit/Higgins-Firefox selectors into components that use this API. Or another API we might agree on in the "Browser Integration Working Group" in the Information Card Foundation.)

Drag a card onto the relyingparty's icon.

How does it work: Well, I had to make another change and add a new parameter to the HTML object of type application/x-informationcard.
<form method='post' action='./infocard' id='infocard' enctype='application/x-www-form-urlencoded'>
<img id="icDropTarget" class="droparea" src="./img/card_off.png" alt=""
onmouseover="this.src='./img/card_on.png';"
onmouseout="this.src='./img/card_off.png';"
onclick='var pf = document.getElementById("infocard"); pf.submit();'/>
<object type="application/x-informationcard" name="xmlToken">
<param name="privacyUrl" value="https://w4de3esy0069028.gdc-bln01.t-systems.com:8443/relyingparty/?privacy.txt"/>
<param name="requiredClaims" value="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/privatepersonalidentifier http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"/>
<param name="optionalClaims" value="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/streetaddress http://schemas.xmlsoap.org/ws/2005/05/identity/claims/locality http://schemas.xmlsoap.org/ws/2005/05/identity/claims/stateorprovince http://schemas.xmlsoap.org/ws/2005/05/identity/claims/postalcode http://schemas.xmlsoap.org/ws/2005/05/identity/claims/country http://schemas.xmlsoap.org/ws/2005/05/identity/claims/homephone http://schemas.xmlsoap.org/ws/2005/05/identity/claims/otherphone http://schemas.xmlsoap.org/ws/2005/05/identity/claims/mobilephone http://schemas.xmlsoap.org/ws/2005/05/identity/claims/dateofbirth http://schemas.xmlsoap.org/ws/2005/05/identity/claims/gender"/>
<param name="tokenType" value="urn:oasis:names:tc:SAML:1.0:assertion"/>
<param name="privacyVersion" value="1"/>
<param name="icDropTargetId" value="icDropTarget"/>
</object>
</form>
The new parameter "icDropTargetId" signifies the element where information cards can be dropped onto. The img element in this example has this id. If the element is inside a form than it is submitted by the dropped information card. Simple!
Enjoy. (with Firefox 2 please)
Posted by
Unknown
at
5:01 PM
0
comments
![]()
Labels: CardSpace4Firefox, drag and drop, information card, Information Card Foundation, openinfocard, xmldap
Wednesday, September 17, 2008
Microsoft PDC2008 - Identity
| Claims-Based Identity: A Security Model for Connected Applications Presenter(s): Kim Cameron, Stuart Kwan | Claims-based security is the underpinning of many applications, services, and servers. This model enables security features like: multiple authentication types, stronger authentication on-the-fly, and delegation of user identity between applications. Learn how to use this model in .NET, how it integrates with Active Directory, how it works across platforms, how it works with existing applications, and how we use it at Microsoft. Tags: Advanced, Cloud Services, Identity |
Live Platform: Identity Services Presenter: Jorgen Thelin | The Live Platform enables developers on any platform to choose the identity integration model that best enables their scenarios, including: web or client authentication, delegated authentication, or federated authentication. Learn how to build seamless, cobranded, and customized sign-up and sign-in experiences. Tags: Expert, Identity, Live Platform |
| Securing Your Service Using the Federated Identity Services Presenter: Justin Smith | Learn how identity services can quickly add authentication and authorization to a service, as well as federate with other identity systems, making it possible for a service to seamlessly use corporate credentials for access control. Tags: Advanced, Cloud Services, Identity |
| Connecting Active Directory to Microsoft Cloud Services Presenter(s): Lynn Ayres, Tore Sundelin | Learn how to augment your existing IT infrastructure with Microsoft Services. Manage and secure end user access to cloud services using your existing investment in Active Directory. Enable end users to access cloud services through existing Active Directory accounts, the same way they access your intranet-hosted software today. Hear how to enable existing software to use new service capabilities without re-writes, and do it all through the use of open and standard protocols. Tags: Advanced, Cloud Services, Identity |
| "Zermatt": Enabling Next Generation Identity | The security demands of applications continue to evolve in the face of compliance requirements, new online threats, and SOA and cloud re-engineering. See how to use the "Zermatt" next-generation authentication framework and services and the claims-based identity model to enable single sign on, strong authentication, federation, and the ability to flow user authentication between applications. Find out how to use "Zermatt" with ASP.NET, WCF, Active Directory, and Windows CardSpace. Tags: Advanced, Identity |
| "Zermatt": Deep Dive | In this session we examine the architecture of "Zermatt" next generation identity technology, and how it can be customized and extended for advanced security scenarios. At the center of the discussion is the Security Token Service (STS), a core component providing authentication and identity services. Many applications will benefit from an embedded STS, and many scenarios will call for an STS that is built on a specialized user store. Tags: Expert, Identity |
| Windows CardSpace "2": Under the Hood | Windows CardSpace provides a consistent, hardened sign-in experience that uses standard protocols and works with both thin and smart client applications. Learn about the features and architecture of the next version of Windows CardSpace. Tags: Advanced, Identity |
| Services Symposium: Enterprise Grade Cloud Applications Speaker information pending. | Today, hosted applications do not offer many of the features that large enterprises expect related to identity, management, and data. See detailed examples of "enterprise grade" hosted application design. Learn how to implement a federated identity scenario, enable remote application management, and provide richer control of data storage. Tags: Advanced, Cloud Services, Identity |
And: No connection between SharePoint and CardSpace/Identity/Zermatt?

Posted by
Unknown
at
10:01 PM
0
comments
![]()
Intel Dude - The Burger Diet
Usually well informed sources hint that ID-TBD has more meanings than expected.
Posted by
Unknown
at
10:01 PM
0
comments
![]()
Labels: idtbd
Monday, September 15, 2008
xmldap STS update
While the service at https://xmldap.org/sts/ currently has an outdated certificate (Sorry!) the code did improve nevertheless.
When you compile and install the code on your server then you can now create managed cards that have the RequireStrongRecipientIdentity and RequireAppliesTo elements set.
I will update the applications on xmldap.org after we have the valid cert again.
The openinfocard id selector was updated too to read and interpret the new element in managed cards.
Enjoy.
Posted by
Unknown
at
11:02 PM
1 comments
![]()
Labels: id selector, openinfocard, xmldap
Friday, September 12, 2008
Firefox Java Plugin(s)
Have you ever wondered how Firefox finds the Java plugin on Windows systems? The reason you might start to wonder is that Firefox finds the plugin even when you installed Firefox after you had installed Java...
The trick is that Firefox - as long as you don't configure it not to do this - scans the Windows Registry.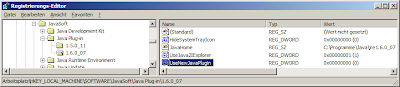
If you experience problems with the new NPRUNTIME version of the Java plugin you can disable it like shown in the picture. This solves problems Java based plugins like the openinfocard id selector have with this new and improved Java plugin.
Please note that this is (somewhat) independent of Firefox. Even if you have an older version of Firefox the new plugin's bugs can hurt you if you have a recent version of Java that contains the new npruntime version of the Java plugin.
I recommend to disable the new npruntime plugin for Java in Firefox.
Posted by
Unknown
at
11:05 PM
0
comments
![]()
Labels: extension, firefox, Firefox extension, java, openinfocard
Tuesday, September 09, 2008
Common Misconception: Username/Password Tokens

People new to Information Cards sometimes think that Information Cards are used to transport username and password to login at a relying party....
Well, Information Cards could be used for that but this is a stupid idea.
First it is incomprehension. Then you start to think: "Why not. This could make the life of a relying party easier. They know how to handle username and password, so let's give it to them". Bad idea.
When you use the security token to transport username and password and you use nothing but username and password from the token then you are giving away the advantages of the whole concept.
There need to be changes to the RP's software to disassemble the security token anyway. When you accept this then you should accept that you can then use the security features of the token too. Each library that can disassemble the token can validate it too. It does not hurt to check the validity dates of the security token. It does not hurt to verify the signature of the security token. If the backend system is so old and inflexible that you must provide two strings for authentication then use a variation of e.g.: uid=PPID, pwd=public-key-base64 or uid=username, pwd=PPID or uid=first-8-bytes-from-PPID, pwd=8-bytes-from-public-key-hash-from-selected-but-fixed-positions. But you must check the signature. Only the owner of the private key could sign the security token and the private key is never transferred to the anybody. This is THE advantage compared to username and password. You can not forge the security token even if you know username and password.
Don't invent username/password-tokens. Don't do evil.
Posted by
Unknown
at
3:39 PM
0
comments
![]()
Labels: information card, security token
Misconception

When I was new to Information Cards I for some time believed that it is possible to use another cert for security token signatures than for the SSL endpoint. This is not true. I thought that this is a feature for the scenario when you host your STS at a webserver provider e.g. at https://openinfocard.org/ and you don't have access to the webserver's SSL key.
During the last days I was reminded of this misconception because https://xmldap.org/sts/ was down and I wanted to deploy the XMLDAP war files to openinfocard.org...
GoDaddy support told me that they can not give me the private key of "my" SSL cert. Bummer.
Without that key I can not issue security tokens. And there is no way to specify that I am using certA for SSL protection of the endpoint and certB to sign the security token. Hm. Maybe this should be possible in the "standard"?
Certs, certs, certs everywhere...
Posted by
Unknown
at
3:15 PM
0
comments
![]()
Labels: certificate, information card
openinfocard and Firefox 3

There are currently issues with java in Firefox3 that prevent the openinfocard id selector to function reliably. For the time beeing: If you want to use/try the openinfocard id selector then please use Firefox 2.0.0.16.
Mozilla and Sun are changing the way java works in Firefox and this seems to be problematic. While I could work around some issues, there is no workaround for others. Using 6u10 makes things worse.
The current problems break all java extensions in Firefox3 that use the jar file loading technique recommended by the Mozilla Developer Center.
Posted by
Unknown
at
2:58 PM
0
comments
![]()
Labels: extension, firefox, java, openinfocard
Über-Org
Yesterday at DIDW world I attended the morning part of the IDTBD workshop; an effort to create a new organisation that is an umbrella for e.g. OpenID foundation, Data Portability Project, Open Web or Information Card Foundation.
While I think that there are good reasons to try and the mission is honorable I think that this will not work as proposed. (I don't have access to the documents...)
In the end the whole thing is about money/funds, power/control and community. And not to forget IPR.
Something that might work, I think, is an organisation that is merely a helper organisation for the other organisations. It provides help to set up a non-profit org, to define bylaws, maybe secretary services, provide financial knowledge, fund raising knowledge, tax knowledge, HR knowledge etc. But this neworg has not power in the "real" organisation. It provides services to the real organistion by helping with issues the techies usually have problems with.
This would be not the big dream neworg but usefull.
Please don't mind this Kindergarden example. In Berlin there is an organisation called "Dachverband Berliner Kinder- und Schülerläden e.V." (DAKS). You could translate this as "Non-profit umbrella organisation of Berlin's Kinder- and Schülerläden". It provides this kind of services to its member Kinderläden. A Kinderladen is a Kindergarden that is run by the parents and not be the local government. Parents are no experts on how to run a Kinderladen and this knowledge gap is filled by the umbrella organisation's services. (The DAKS sees itself as a politcal representative of the 650 Kinderlädern in Berlin also).
Posted by
Unknown
at
1:08 PM
0
comments
![]()
Information Card Directory

There is still a lot to do to promote Information Cards. Fun Communications GmbH - member of the Information Card Foundation - has a directory of Information Card RPs and Issuers here at http://www.informationcarddirectory.com/.
We need to:
- put Information Card support in wide spread applications
- Joomla
- Wordpress
- Mediawiki
- ...
- put Informaton Card support into browsers
- Firefox
- Opera
- Chrome
- Webkit based browsers
- Mobile browsers
- ...
- put Information Card support into frameworks, APIs, middleware and widespread servers
- JAAS
- apache mod_auth_infocard
- PAM (pluggable authentication module)
- SAP
- ...
- put Information Card support into mobile devices
- cardstore on SIM/UICC/javacard...
- card selector on phone while browsing on PC
- ...
- Have major sites issue and accept Information Cards
- Blogger.com
- eBay / Paypal
- Yahoo
- LiveId
- Press / Banks / Government Services
- ...
- Improve Information Card usability
- Faster startup of selector
- Default card for a site
- security token caching/reuse
- even better privacy (U-Prove)
- ...
- Educate / Inform / Convince
- Users
- Developers
- Product managers
- CISOs / CIOs
- Privacy Advocates/Officers
- Auditors
- ...
- ...
Pick your priority...
Posted by
Unknown
at
12:09 PM
0
comments
![]()
Friday, September 05, 2008
Google Chrome

A quote from Wikipedia about Google Chrome:
Plugins
Plugins such as Adobe Flash Player are typically not standardised and as such cannot be sandboxed like tabs. These often need to run at or above the security level of the browser itself. To reduce exposure to attack, plugins are run in separate processes that communicate with the renderer, itself operating at "very low privileges" in dedicated per-tab processes. Plugins will need to be modified to operate within this software architecture while following the principle of least privilege.
Chrome supports the Netscape Plugin Application Programming Interface (NPAPI), but does not support the embedding of ActiveX controls. Also, Chrome does not have an extension system such as Mozilla-compatible *.xpi cross-platform extension architecture and thus XPI-based extensions such as AdBlock and GreaseMonkey can not be adapted to Chrome.
This means: no easy way to port the openinfocard id selector nor the browser add-on to Google Chrome.
Maybe I should take some time to revive my openinfocard plugin subproject...
Or I should start to put IDentity In the Browser and change the Chrome source code...?
Posted by
Unknown
at
1:48 PM
2
comments
![]()
Labels: extension, Google Chrome, openinfocard, plugin
Tuesday, September 02, 2008
Change
Whoever it may concern...
Since beginning of this month I am working for "Deutsche Telekom AG, Laboratories".
Good bye T-Systems, see you.
My desk did not change; Nor did my telephone number(s).
I expect some bumps with my email addresses. The T-Systems address will go away soon and it is still unclear whether I can keep my telekom.de email address. (Mysteries of Microsoft Exchange?)
My work will stay the same. Good!
Posted by
Unknown
at
9:27 AM
0
comments
![]()


