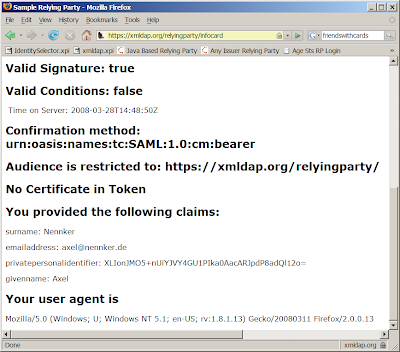
You might have noticed that sometimes the security token on xmldap's relyingparty is not valid. The conditions on the token are not met because the time on the server was about 30 minutes off.
Chuck corrected this immediately and I wanted to verify that the relyingparty there now accepts a security token produced by the latest openinfocard id selector. I quickly installed it, but booom; it failed.
The line of code in question was unnecessary anyway so I cleaned up the javascript quickly; transferred the code from my lab machine to my office machine. Now the installation of the xpi went through but this time the token produced was "undefined". Strange. I did tests this on my lab machine yesterday; so what is the difference between the two machines?
Well, it turns out that the office machine had version 1.0.6 of the CardSpace for Firefox extension. After updating it to the current version 1.0.9 everything now works fine. ... Well, the certificate on xmldap.org expired two days ago. Argh, will be fixed soon. Sorry.
That was a nice 5 Minute adrenalin shock.
Monday, March 31, 2008
Interflop
Posted by
Unknown
at
3:55 PM
1 comments
![]()
Labels: CardSpace, FriendsWithCards, interop, openinfocard, xmldap
Friday, March 28, 2008
in synch
Just synched up the two projects openinfocard and Cardspace for Firefox.
Both are now using the same object handling code. This is the part that implements the id selector selector and the object handling.
Please download the latest openinfocard id selector here.
SharpSTS with CardSpace for Firefox and anon id selector advertising
SharpSTS with openinfocard id selector
Both id selectors installed in the same Firefox profile
Please download the latest version of CardSpace for Firefox here.
Three releases today... Sorry for that.
1. dynamic object handling
2. handle existing but empty parameters like optionalclaims=""
3. better id selector advertising and synch with openinfocard
Posted by
Unknown
at
4:20 PM
2
comments
![]()
Labels: codeplex, CS4FF, id selector advertising, id selector selector, openinfocard
Dynamic objects
Last autumn when a change in Firefox forced us to change the HTML object tag handling we kicked XBL and used DOM event handlers as the primary mechanism to detect and handle objects of type application/x-informationcard.
At that time the three id selectors that use this same piece of code openinfocard, CardSpace for Firefox (on codeplex) and DigitalME stopped working on sites that dynamically create or change the objects of this type.
Yesterday Barry from the SharpSTS project contacted me that his site does not work with "my" extensions... Well, at first I was reluctant to put too much work into supporting this javascript kungfu but Mike Jones persuaded me.
As it turn out it was not that much work as I expected.
Please download the new version from the codeplex site here.
A new version of the openinfocard id selector will be available soon too.
Here are some sites that now work again with the Firefox extensions:
FriendsWithCards
SharpSTS
Kim's Identityblog
These interop tests were done with Firefox 2.0.0.13 and CardSpace (.NET3.5).
Posted by
Unknown
at
1:53 PM
0
comments
![]()
Labels: CardSpace, codeplex, DigitalMe, Firefix, openinfocard, xmldap
Monday, March 24, 2008
openinfocard plugin vs extension
I have no shame... and must tell that a first step in realizing the openinfocard selector as a Firefox plugin instead of an extension was achieved today. A Firefox plugin is probably the correct way to handle HTML <object type="application/x-informationcard" >...</object> inside Firefox.
When I implemented the certificate chain validation I had to build my own Firefox browser from sources because I needed an API that is not in the Gecko SDK but in the Firefox source code. Now I had everything to build a plugin and gave it try.
Today I have an very early version of an openinfocard id selector as a plugin ready.
Posted by
Unknown
at
2:29 PM
0
comments
![]()
Labels: firefox, Firefox plugin, NSAPI, openinfocard
Thursday, March 20, 2008
Certificate Chain Verification for CardSpace
When Microsoft released .NET3.5 changes were made that are not that much visible on the surface. One of these changes is the verification of certificate chains. Formerly only certificates were "validated" but not up to the root certificate through the certificate chain. Mike Jones was so kind to notify me of this improvement and provided the (preliminary) documentation to implement this; and Caleb Baker clarified details where the documentation was indeed "preliminary". Thanks.
Today I am proud to announce a new version of the Firefox extension that enables support for CardSpace. It was tested with and without SSL and on .NET3.0 and .NET3.5 installations. It can live next to the openinfocard extension. Both extensions have in-browser selector selector capabilities. Both extensions advertise the id selector if the user requested this feature on the options page.
Implementing this reminded me of how much work the team around Kim Cameron has put into CardSpace and how well they did it and still do. Applause and thank you.
Posted by
Unknown
at
10:59 PM
0
comments
![]()
Labels: CardSpace, Firefox extension, openinfocard
Friday, March 14, 2008
RSA User centric identity interoperability

"Interoperability Demonstrations
Tuesday, April 8 and Wednesday, April 9, 2008
11:00 AM – 6:00 PM
Moscone South, Mezzanine Level
Purple Room 220
OSIS User centric identity network interoperability between identity providers, card selectors, browsers and websites demonstrates how users can ‘click-in’ to sites via self-issued and managed information cards, or i-cards. Open ID, Higgins Identity Framework, Microsoft CardSpace, SAML, WSTrust, Kerberos and X.509 components interoperate within an identity layer from open-source parts."
Which, of course, include the openinfocard identity selector.
Posted by
Unknown
at
9:36 AM
0
comments
![]()
Labels: interop, openinfocard, openinfocard interop, osis, rsa, rsa2008
Monday, March 10, 2008
openinfocard logo
<Update count="2">

The top three logos are licensed under a Creative Commons Attribution 3.0 Unported License.
</Update count="2">
<Update>: Um... The two logos probably violate the usage guidelines of the information card icons...
So let's use this logo
</Update>
Projects seem to need a logo. I hope that this quick (non-art) work finds some supporters. 
Or should should it be this one?
Posted by
Unknown
at
6:06 PM
3
comments
![]()
Labels: firefox, informationcard, logo, openinfocard
Friday, March 07, 2008
openid with smartcard support
Today I learned about TrustBearer (thanks Berend). TrustBearer combines openid authentication with smartcard authentication. Setting this up is very easy.
1) sign up for an openid at http://openid.trustbearer.com/

2) pair your cert with the new account
You have to install a Firefox extension that does the certificate stuff.

3) logged in and ready to go

4) try it at a openid consumer

5) present your openid and smartcard
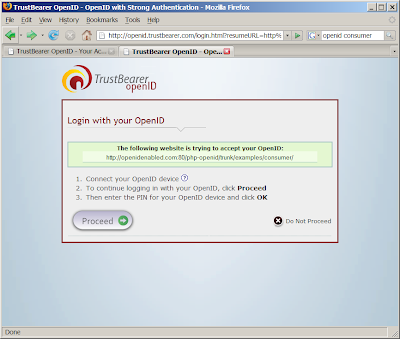
6) nice

Still what I like most in this use case is that the certificate is on the mobile phone. (We integrated these technologies during our project "CardSpace for Telcos" for Deutsche Telekom Laboratories.)
True, these phones are not very much available today but e.g. every New Yorker who participates in the metro field trial can now use the mobile phone not only to pay his metro ticket but also to make the authentication a little bit more secure (no password involved here. Wait: no information card involved either. doh. No Anti-Phishing, no unlinkability, no untracebility).
Anyway, nice.
Posted by
Unknown
at
4:44 PM
3
comments
![]()
Labels: authentication, multifactor, nfc, OpenId, smartcard
Thursday, March 06, 2008
Microsoft acquired Credentica
This is such a smart move of Microsoft! I am impressed and I am sure that Credentica's technology will lead to a privacy improved version of CardSpace. I hope that Microsoft will provide open access to this technology for others to implement identity selectors, relying parties and security token servers. CardSpace is token agnostic but when I have read the U-Prove papers correctly then there is more then one roundtrip between id selector and STS required to deliver all the nice features. The protocol between id selector and STS thus probably has to be changed.
"Nice features": Some weeks ago somebody asked me "What is this (group signatures, zero knowledge based algorithms, electronic money based algorithms) good for. Where can anonymity, privacy, pseudonyms, untracebility, unlinkability, ... be used". At that time I answered this questions on a too technological level, interpreting the word "where" to mean protocols, signatures, encryption. The better answers would have been, and the acquisition of Credentica by Microsoft points in this direction: If the technology in available on every desktop computer or mobile computer/phone then users will learn to want privacy, untracebility and unlinkability. The services a company offers must have these features then or the users will use services that provide them.
Posted by
Unknown
at
9:50 PM
0
comments
![]()
Labels: CardSpace, Credentica, Microsoft, privacy, unlinkability, untracebility
Wednesday, March 05, 2008
CeBIT 2008: CardSpace no matches found
Searching for the term "CardSpace" in the CeBIT search application yields "no matches found" :-(
I know that companies are presenting CardSpace / information card solutions...
And Microsoft's Tom Köhler told the press that Microsoft will announce a trusted partner for identification at CeBIT 2008. Interesting.
Posted by
Unknown
at
7:03 AM
0
comments
![]()
Labels: CardSpace, CeBIT, Trust Center
Monday, March 03, 2008
SAML ECP Firefox Extension
| This is cool. I was thinking of giving this a try myself. An identity selector that speaks SAML instead of WS-*. This should not be that complicated when you mix the openinfocard selector with a java SAML library. Add ingredients, shake well, stir, ready. I am wondering if they took the photo shot before or after they began this project. |
Posted by
Unknown
at
11:47 PM
0
comments
![]()
Labels: firefox, informationcard, liberty alliance, openinfocard, SAML
First European Identity Award
The award will be given in six categories:
- Best innovation in Identity Management
- Best new standard/improved standard in Identity Management
- Best project within the last 12 months: Internal use of Identity Management
- Best project within the last 12 months: B2B use of Identity Management
- Best project within the last 12 months: B2C use of Identity Management
- Best project within the last 12 months: Identity Management in eGovernment
We kindly ask you to make proposals for the latter four categories. Each proposal shall consist of a one page description of the project explaining the project and why the project is, from your point of view, a candidate for the award.
The project has to have been finalized within the last 12 months.
The jury will consist of KCP analysts. The awards will be handed during an evening event at the EIC 2008.
For sure there will be journalists and we will provide press releases about the award.
We will take nominations until March 10th, 2008. Email your nominations directly to Martin Kuppinger.
Please clarify whether the nominees will be available for a best practice presentation during EIC 2008. We would like to see the winners and some close followers as best practice presentations."
Posted by
Unknown
at
3:05 PM
0
comments
![]()
Labels: eic, eic2008, identity management
Saturday, March 01, 2008
IdentityCampBremen
| This sounds interesting. "Identitycamp Bremen will be the first Barcamp in Germany that focuses on identity 2.0, single-sign-on, reputation management, relationship management, privacy 2.0 and related issues." |
The new ePA and its pseudonym feature should be talked about then too. We should help to build the need-to-know society. We should use claims instead of identification.
Posted by
Unknown
at
8:49 PM
0
comments
![]()
Labels: identity, privacy, relationship management, reputation management, single-sign-on