While musing about reputation and trustworthyness of information I came across http://www.trustme.com/. They provide you with a disposable temporary email address that is valid for 15 minutes. This seems quite usefull if some RP requires to know your email address before it serves out some information like e.g. a whitepaper. Now you can receive that one-time-link from the RP, use it for email-verified-login, download that paper and forget the RP again.
But why is trustme.com doing this? Altruism?
Can I trust Steve Cannon, 5699 Kanan Road #115, Agoura Hills, CA 91301, US not to read my temporary email? What is his reputation? Probably his address is outdated anyway?!
Monday, April 28, 2008
Disposable Temporary E-Mail Address
Posted by
Unknown
at
10:54 AM
0
comments
![]()
Labels: reputation, security, trust
Thursday, April 24, 2008
Card Selector on Windows Mobile
I just heard a very interesting talk given by Dr. Bruno Quint from Corisecio. They implemented an id selector on windows mobile. So you are able to surf on the windows mobile device and use this selector when information cards are accepted by a RP. And they implemented a connection between your PC and the windows mobile device, so that you now can surf the Web on any PC and use your information card selector on your mobile device.
Corisecio also added smartcard support on the mobile device which makes this an extra strong solution.
To bad that Corisecio does not participate at the OSIS interops. Unlikely that Dr. Quint does not know about OSIS. I will ask him during the break.
I guess this stuff is still smoking because it is so new.
Posted by
Unknown
at
11:44 AM
0
comments
![]()
Labels: id selector, information card, mobile, windows mobile
Tuesday, April 22, 2008
EIC2008 Workshops
This morning I was at the VRM unworkshop at the EIC2008 conference. What I understood there was that VRM is about principles for service providers that serve my claims.
- what are the logging and privacy contraints ?
- can administrators see my data ?
etc
Whether this concept will be a success, I don't know. I think that most users don't understand what and how much and to whom and under what conditions they should give away claims or not. So in the sense of making a deal with the web-shop (I give you claims and you don't bother me with advertisements that make no sense to me) I think that this is desirable but I think that most users will give away too much claims with uncertain conditions what the RP does with this data.
Later I joined the Liberty Alliance Standards workshop. Interesting talks there too. One talk I really liked was the one from my colleague, Michael Gärtner, who demoed the federation from a T-Home online account to a T-Mobile account. This facilitates the current connection the user uses to protect the login. So if you are using your home DSL connection then this access is used as a second factor for your T-Home account. And If you have a T-Mobile internet connection using your mobile phone then that access is used as a second factor for your T-Home authentication. I like that.
Posted by
Unknown
at
2:46 PM
0
comments
![]()
Monday, April 21, 2008
OSIS Interop Showcase at EIC2008
Wednesday and Thursday are the days to be in Munich to attend the 2nd European Identity Conference. Kuppinger and Cole were so kind to provide space and a WLAN and time and marketing people for the first post RSA interop. We will demonstrate interoperability during the last two hours of the expo opening time each day. Most of the RSA interop sites are up and working. The results of this interop go into the main RSA results table.
Tomorrow (Tuesday) is the day of interesting pre-conference workshops. I will attend the workshop "VRM 2008 - Unconference on Vendor Relationship Management" unorganized by Doc Searls. My colleague from T-Home, Michael Gärtner will present at the Liberty Alliance Standards Workshop. My colleague, Jörg Heuer, will participate in this panel discussion.
Posted by
Unknown
at
9:47 AM
0
comments
![]()
Labels: eic2008, interop, openinfocard, osis, xmldap
KeeLoq Broken
KeeLoq, the major remote keyless entry system for cars and buildings is hacked - again.
The CryptoLab of Ruhr University Bochum published an attack on the most widely used remote keyless entry system. The researches used a differential power analysis to recover the manufacturer key. With that key all you need is two messages between the key and the door/car. These messages can be picked up from 100m away. Knowing the manufacturer key allows for creating an arbitrary number of valid new keys and generating new remote controls.
This is a new attack and should not be confused with an older ones.
Posted by
Unknown
at
9:26 AM
0
comments
![]()
Thursday, April 17, 2008
cmort@ssosummit
Today I received an email that advertises the ssosummit.
- The Multiple Facets of SSO - Patrick Harding, CTO, Ping Identity
- A Business Case for ESSO - Ken Tyminski, Retired CISO of Prudential Insurance
- Federated Identity Communities in Action - Dave Miller, Chief Security Officer, Covisint
- Web Services Single Sign-On: There and Back Again - Gunnar Peterson, Managing Principal, Arctec Group
- Why SSO and Provisioning Impact the SaaS Value Prop - Chuck Mortimore, Director of Platform Services, Rearden Commerce
- More to come……
So... for some first hand experience from the experts in both SSO and snowboarding: Come to Keystone.
On the other hand it is in July. So you will probably find more SSO than snowboarding. Speaking of "ice and snow": You could participate in the Liberty Alliance plenary meeting in Stockholm, Sweden from July 8-10 to find some connectid too.
Monday, April 14, 2008
OSIS Interop Brute Force

Pat Patterson brute-forced the OSIS Interop Event and finished all the tests for the opensso solution. Unbelievable work!
I am wondering what this means for the xmldap RP because opensso uses the xmldap libraries. The results should - more or less - show some similarity...
The federated_identity site uses symmetric binding which is not supported by xmldap.
Siemens IdP: Have to look into this.
Thursday, April 10, 2008
Wednesday, April 09, 2008
IT-Security Made in Germany
I want to encourage you to talk to the people in booth 1332 at the RSA expo. Several German companies created "IT-Security Made in Germany" and actually they are doing interesting stuff. My current favorite is a smartcard on a microSD card (CertGate) that you can put in (almost) any mobile phone to get smartcard support on your phone. It is not the silver bullet for the identity management problems I would like to solve but certainly interesting. Or talk to Manuel Bach (BSI) about the eCard API. Definitely this is something to watch.
My First Italian Spam
Today I received my first spam email in the Italian language. What does this say about spammers sending this to a ".de" email address? What does it say about the success rate of spam?
Well, what a luck that I can only guess the meaning of this italian lure. Now it goes the same way as the latest Liberian business opportunities, Nigerian heritages and eBay invoices; to the trash can. I haven't got a "your password needs to be reset"-email or a "your credentials need to be verified"-email for a long time. Identity theft on the decline? Or is spam filter finally "working"?
Von: Banca di Roma Online [mailto:servizionline@unicreditbancaroma.it]
Gesendet: Mittwoch, 9. April 2008 12:47
Betreff: Verifica Urgente Di Cliente !
Gentile cliente ,
Recentemente abbiamo determinato che i calcolatori differenti avessero entrato al vostro cliente di inseguimento ed i guasti multipli di parola d'accesso erano presenti prima degli inizio attività.
Vi preghiamo di confermare che il vostro conto e ancora attivo si che funziona in parametri normali.
Se questo non è completato entro 11 aprile 2008, saremo costretti a sospendere indefinitamente il vostro cliente, come può essere usato per gli scopi fraudolenti. Grazie per la vostra cooperazione.
Per confermare tutte queste click sul seguente link: .
Cliccate qui per andare alla pagina dell`autorizzazione »
Considerazioni migliori,
Il reparto sicurezza
--------------------------------------------------------------------------------
Grazie per la vostra attenzione rapida a questa materia.
Chiediamo scusa per eventuali inconvenienti. Grazie per usando i Di Roma di Banca!
Posted by
Unknown
at
2:18 PM
1 comments
![]()
Labels: identity theft, spam
Tuesday, April 08, 2008
RSA WLAN slooow. or: bearer vs. holder-of-key
Trying to commit a change to the xmldap STS that makes it obey the subject confirmation method element in the RST.
BUT:
$ ping openinfocard.googlecode.com
Ping googlecode.l.google.com [64.233.187.82] mit 32 Bytes Daten:
Antwort von 64.233.187.82: Bytes=32 Zeit=348ms TTL=241
Antwort von 64.233.187.82: Bytes=32 Zeit=2787ms TTL=241
Antwort von 64.233.187.82: Bytes=32 Zeit=1318ms TTL=241
Ahhh. The fourth try to commit the files succeeded.
Please find the new version in the xmldap source code repository at the openinfocard project site.
Posted by
Unknown
at
7:37 PM
0
comments
![]()
Labels: bearer, holder-of-key, openinfocard, rsa, rsa2008, subject confirmation, xmldap
Atmel Proprietary Cryptographic Algorithm
Making progress with my jet lag and awoke at 4 am this night...
Sorting through the papers that were in the RSA conference Alan Turing knapsack...
And found this piece from Atmel:
CryptoMemory
...A proprietary cryptographic algorithm encrypts data, passwords and checksums, providing a secure place for storage of sensitive information. With its tamper protection circuits, this information remains safe even under attack.
...
Two things about this:
1) "proprietary encryption"??? Hello!?
This leads most likely leads to desaster. Allways. Don't people learn?
2) If it is tamper resistant why don't say what FIPS 140-2 level or EAL certification it has?
This sheet is in the trash can now.
I don't understand this. Atmel has build cool things for a long time. Why are they doing this?! Was not AES designed to run on chips?
Posted by
Unknown
at
2:58 PM
0
comments
![]()
Labels: AES, proprietary crypto, rsa, rsa2008, snake oil
CISSP at RSA
Please excuse this off-identity post, but finally I received the notification that I am a CISSP now. For sure I will get a nice piece of cardboard to hang next to my CISA certification. Great.
Maybe I can rescue this post by writing that I can now collect CPEs at the RSA conference that I am currently attending. The first workshop day was already quite interesting. Ashish Jain showed how he can use an information card and SAML2.0 to login to google apps. Super cool. Congratulations.
Robert Temple from BT (not Banker's Trust) talked about SAML2.0 at BT. Very interesting. I hope to get the slides soon. Conor P. Cahill gave an interesting presentation. I believe in the mobile phone as a secure (authentication) device too. Let us build the magic wand for identity.
Posted by
Unknown
at
12:23 AM
0
comments
![]()
Labels: cisa, cissp, magic wand, SAML
Monday, April 07, 2008
OSIS Interop Media Alert
Shamelessly copied from Johannes Ernst's blog.
FOR IMMEDIATE RELEASE
April 7, 2008
MEDIA ALERT
Showcasing How Users Can Control their Identity Online, Industry's Largest Identity Interoperability Demonstration Scheduled for RSA 2008
Fifty-seven member open source identity group to test and demonstrate interoperability between user-centric identity protocols and providers
SAN FRANCISCO (RSA Conference 2008) - April 7, 2008 - Open Source Identity Systems (OSIS) will conduct the largest user-centric identity interoperability test and demonstration at the 2008 RSA Conference, April 7-11 at the Moscone Center in San Francisco. The 33 member organizations and 24 projects of OSIS will showcase network interoperability between identity providers, card selectors, browsers and Web sites, demonstrating practical uses for user-centric identity technology, including how users can "click-in" to Web sites via self-issued and managed Information Cards and OpenIDs. The user-centric identity model gives consumers greater control and security over their identity information, allowing them to determine how sensitive identity information should be shared at each visited Web site.
During the demonstration, OSIS members will illustrate interoperability between Information Card and OpenID software, the technologies behind user-centric identity.Features being demonstrated include:
* Enabling people to control what identity information is disclosed about them
* Portability of digital identities across software and platforms
* Management and use of Information Cards and OpenIDs
* Information Cards used with OpenIDs to enable phishing-resistant sign-in to Web sites
WHO:OSIS, a working group of Identity Commons (please see below for a list of companies and projects). Members of the group are committed to a goal of Internet identity interoperability across projects, protocols, companies and platforms.
WHAT:OSIS User-Centric Identity Interoperability Demonstration at RSA 2008
WHERE: RSA Conference, Moscone Center South, San Francisco, Mezzanine Level, Purple Room 220
WHEN:Tuesday, April 8 and Wednesday, April 9; public working sessions 11 am to 4 pm, demonstrations 4 pm to 6 pm
About OSIS
Open Source Identity Systems, a working group of Identity Commons, brings together many identity-related open-source and commercial projects, and synchronizes and harmonizes the construction of an interoperable identity layer for the Internet from open-source parts and software that interoperates with them. For more information on OSIS, visit http://wiki.idcommons.net/index.php/OsisCharter.
OSIS participating companies:
* AOL
* ATE Software
* CA
* Cordance
* Fraunhofer FOKUS
* FuGen Solutions
* Fun Communications
* Google
* IBM
* JanRain
* LinkSafe
* Microsoft
* NetMesh
* Novell
* Nulli Secundus
* ooTao
* Oracle
* Orange
* Parity
* Ping Identity
* Plaxo
* Siemens
* SixApart
* Sun Microsystems
* Sxip Identity
* Thinktecture
* ThoughtWorks
* TrustBearer Labs
* VeriSign
* Vidoop
* WSO2
* Yahoo!
* Zend
Projects and Organizations:
* Bandit Project
* Codeplex
* DiSO Project
* Dominck Baier
* Drupal
* Francis Shanahan
* Higgins Project
* I-names
* Identity Commons
* Information Cards
* LID
* OpenID
* OpenInfocard
* OpenSSO
* Open XRI
* Pamela Project
* Rob Richards
* Sharp STS
* SignOn.com
* SourceID
* Shibboleth
* Verisign Personal Identity Provider
* Xmldap
* Yadis
All company/project names and service marks may be trademarks or registered trademarks of their respective companies/organizations.
OSIS Participants Contact Information:
http://osis.idcommons.net/wiki/Category:Participant
Media Contact:
Charlotte Betterley
Novell
(781) 464-8253
cbetterley@novell.com
Posted by
Unknown
at
3:47 PM
0
comments
![]()
Labels: openinfocard, osis, rsa, rsa2, xmldap
Friday, April 04, 2008
RSA Personal Schedule
RSA Conference 2008
| Personal Schedule for Axel Nennker |
| Sunday |
|
|
|
|
| Monday | ||
|
| ||
|
| ||
| 9:00 AM-12:30 PM | SEM-M01 | Concordia Project: Interoperable Answers to Real-World Identity Deployments |
| 1:00 PM-4:30 PM | SEM-M03 | Liberty Alliance: Identity Federation and Web Services: Happening Today - Enabling Tomorrow |
| Tuesday | ||
|
| ||
|
| ||
| 8:00 AM-8:45 AM | KEY-101 | The Role of Security in Business Innovation: From Villain to Hero |
| 8:45 AM-9:30 AM | KEY-102 | Information Centric Security: The Next Wave |
| 9:45 AM-10:25 AM | KEY-103 | Enabling End-to-End Trust |
| 11:00 AM-1:30 PM | Personal Meeting | Identity Interop |
| 1:30 PM-2:40 PM | DEF-105 | The Seven Most Dangerous New Attack Techniques, and What's Coming Next |
| 2:40 PM-3:00 PM | Personal Meeting | Identity Interop |
| 3:00 PM-3:50 PM | IAM-106 | Digital Identity and Service-Oriented Architecture - Hope and Glory |
| 3:50 PM-7:00 PM | Personal Meeting | Identity Interop |
| Wednesday | ||
|
| ||
|
| ||
| 8:00 AM-8:50 AM | IAM-201 | Breaking the Identity Metasystem |
| 9:10 AM-10:20 AM | IAM-202 | Enterprise Access Management: The XACML Standards-Based Path Ahead |
| 11:00 AM-4:00 PM | Personal Meeting | Identity Interop |
| Thursday | ||
|
| ||
|
| ||
| 8:00 AM-8:50 AM | AUTH-301 | Authentication in the Mobile World |
| 10:40 AM-11:50 AM | AUTH-303 | Deep Inside the New OATH Reference Architecture |
| 1:40 PM-2:30 PM | P2P-305A | Securing VoIP Networks |
| 2:45 PM-3:35 PM | P2P-306B | Security Management: Building a Functional Risk Framework |
| 4:05 PM-4:50 PM | KEY-308 | Viewing the World Through a Different Prism |
| Friday | ||
|
| ||
|
| ||
| 9:00 AM-9:50 AM | AUTH-401 | Experiences Validating Secure Open Source User-Centric Identity Systems |
| 10:05 AM-10:55 AM | P2P-402A | User-Centric Identity and the Enterprise: Promise, Pitfalls and REALITY |
| 11:10 AM-12:00 PM | P2P-403A | Will User-Centric Identity Increase Internet Security and User Convenience? |
| 1:30 PM-2:15 PM | KEY-405 | The Hugh Thompson Show LIVE at RSA! |
Posted by
Unknown
at
2:32 PM
0
comments
![]()
Tuesday, April 01, 2008
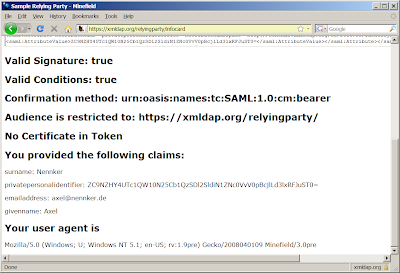
Minefield defused
The openinfocard id selector now works with Firefox3.
The bug in Firefox3 is not fixed but circumvented. Firefox3 treats arrays of java objects differently than before.
In a javascript script the call "java_method([aElement])" formerly worked but now it fails. It has to be replaced with
var urlArray = java.lang.reflect.Array.newInstance(java.net.URL, 1);
urlArray[0] = aElement; // aElement beeing a java.net.URL
java_method(urlArray);
Please download the latest version in the openinfocard download area.
Posted by
Unknown
at
3:27 PM
0
comments
![]()
Labels: firefox, firefox3, javascript, openinfocard
Firefox3 Java Bug: openinfocard needs your help

The early betas of Firefox3 crashed when the openinfocard identity selector was loaded. The current beta and the one before do not crash, but don't work.
file:/C:/Dokumente%20und%20Einstellungen/Nennker.Axel/Anwendungsdaten/Mozilla/Firefox/Profiles/kb7ofbop.default/extensions/
%7B211DBAEA-CE99-11DA-8254-96BEC52F3316%7D/components/firefoxClassLoader.jar
to Java value of type java.net.URL[]
Yesterday I retrieved the latest Firefox3 code from CVS and noticed that now it is called "3.0pre1", but still it has the same bug.
Openinfocard needs your help. Please try this with other versions of java on different operating systems and report this on the bugzilla page for this bug.
Here is a version of the openinfocard id selector that installs on Firefox3.
Here is the latest nightly Firefox3. Here is the latest beta.
I don't want Firefox to be in a pre version with this bug inside. Please help! Report and confirm this bug here.
Posted by
Unknown
at
8:12 AM
0
comments
![]()
Labels: bugzilla, firefox, java, openinfocard