You will find this interessting: http://blogs.msdn.com/card/
Wednesday, September 26, 2007
CardSpace Team Blog
Posted by
Unknown
at
2:51 PM
0
comments
![]()
Labels: CardSpace
Tuesday, September 25, 2007
2007 IDDY Award goes to Rearden Commerce
Chuck Mortimore today received the 2007 IDDY Award of the Liberty Alliance Project on behalf of Rearden Commerce. Chuck is the original author of the openinfocard id selector and the xmldap STS an RP. Congratulations!
Posted by
Unknown
at
5:59 PM
0
comments
![]()
Labels: "IDDY 2007" openinfocard
Win an iPhone
The Bandit Project gives you the chance to win an iPhone if you get an Information Card here: https://cards.bandit-project.org/
So... You don't care about Information Cards and just want that iPhone? What is the shortest way to this goal?
If you have Windows Vista, then this is easy. Everything will just work out of the box.
If you have an older version of Windows or an "alternative operating system", then download the best browser on earth: Firefox and get an Id Selector e.g. the openinfocard id selector or something from here.
If you have Windows XP, then as an alternative way you might get IE7 and .NET3. And don't forget to visit update.microsoft.com afterwards.
Thanks to the Bandit Project for this promotion of information cards.
BTW: If I win, I would prefer the T-Mobile version. :-)
Posted by
Unknown
at
4:11 PM
0
comments
![]()
Monday, September 24, 2007
DIDW 2007 09 24 WLAN
This is off topic, but I am astonished by the number of WLAN access points "visible" in my hotel room. Maybe an error in my WLAN software?
Posted by
Unknown
at
10:06 PM
0
comments
![]()
Friday, September 21, 2007
IA Management
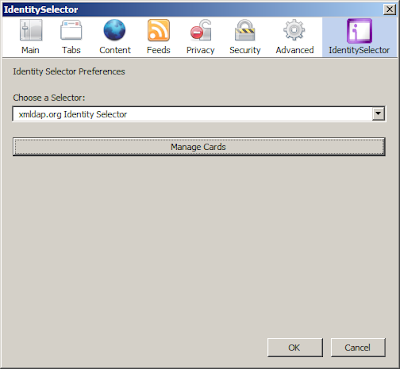
The openinfocard id selector now has a "Manage Cards" button on its preferences page.
The preferences are displayed when you choose the menu item "options" from the "tools" menu. Pressing the "Manage Cards" button opens the same window that pops up when you visit a relying party. You can create and delete self-issued cards from here and you can import and delete managed cards from here. You can't (currently) retrieve the values of a managed card from this dialog.
The new version (xmldap-0.9.8.200709212108.xpi) of the openinfocard id selector can be found here. I will update the version number to 0.9.8 after I added some more features; like displaying the privacy statement. This can't currently by done because Kevin Miller's Firefox extension uses privacyPolicy instead of privacyUrl and privacyPolicyVersion instead of privacyVersion. (And because the openinfocard id selector uses Kevin's selector selector.) I hope that either Kevin or Garrett will fix this soon.
Another needed feature for the openinfocard id selector is "phishing defense". This should not be too complicated to implement, but will make an update of the internal card store format necessary.
Anyway: Manage your cards!
Posted by
Unknown
at
11:11 PM
0
comments
![]()
Labels: openinfocard firefox extension
Thursday, September 20, 2007
Smartcards as a trusted security anchor
Today I am attending a CAST workshop about smartcards and their use to solve security problems.
The first talk is held by Michael Senkbeil from the Sparkassen Informationszentrum.
They have 64 million smartcards issued in Germany.
These cards are mandatory in Germany if you want to buy cigaretts. The card is used to proof that the buyer is old enough to buy cigaretts.
Mr. Senkbeil will tell us today how this scenario can be transferred to Internet usages.
First the user needs a smartcard reader and a browser plugin. Get the Plugin for Firefox here.
The browser plugin is triggered by the relyingparty. It contacts the smartcard and gets encrypted data from the card that it transfers to the relying party. The relying party has (multiple) server cards that decrypt the data and present the readable content to the RP. The server card(s) are issued by the Sparkasse too.
Phishing protection is not a main feature of this solution.
Mr. Senkbeil recomments to add this mechnism to the "normal" username/password scenario. If the card gets lost then there is no additional security on the card. It is not PIN-protected. So everybody can use the card. To minimize this risk he proposes to use a password in combination with this new scheme.
Feature list:
- age verification
- Laden der Geldkarte
- Internet Login
Q&A:
Q: Is this a Sparkasse only solution?
A: No. Every german "EC-Card" should work.
Q: API
A: PC/SC
Q: Demo had no password input
A: Card number is the userid. The password is the password of the relying party.
The password needs not be used.
Q: is the plugin signed
A: Yes it is.
Q: Profiling? Linkability.
A: is possible. The card number is a unique number.
My comment: This is not good. We need to integrate this with CardSpace.
Q: How does the user recognize the server? How does he verify that the server is the true one?
A: SSL. The proposed solution has no mutual authentication.
Q: How does the challenge-response mechanism work?
A: The RP generates a challenge that is used by the card. The plugin transfers the challenge to the card and receives an encrypted block of data. The RP has cards too, that decrypt the data and compare the challenge.
Q: Sparkassen Internet Banking: Will the Sparkassen use this mechanism to secure it's own internet banking?
A: A new class of smartcard reader is currently worked on. This will be released to the public next year.
Comment: This answer means: No.
Q: Is the cryptography symmetric or asymmetric?
A: Symmetric with derived keys.
Smartcards for Tachographs
The second talk is held by Mr. Klaus-Peter Schmidt from Sagem-Orga GmbH.
Security Evaluation of Smartcards
The third talk is held by Mr. Detlef Kraus from SRC Security Research & Consulting GmbH.
Crypto Algorithms for Environments with limited resources
The fourth talk is held by Mr. Axel Poschmann from the Ruhr-University of Bochum.
CPU-Market: PCs 0,2% -- embedded systems 99,8%
Smartcards: 8Mhz, 8bit, a few kilobytes memory
Metrics and tradeoffs for light-weight crypto
- security
- low cost
- performance
Mr. Poschmann explains the features of PRESENT (an ultra-lightweight block cipher).
The Identity of the Connector
Talk by Dr. Jens Urmann from InterComponentWare AG about a part (the connector) of the German health care system infrastructure. -> This usally gets messy really quick if you dive into the details... (not blog compatible)
Security anchors for mobile devices
Mr. Michael Kasper gives an overview over xSIM architectures.
- USIM
- MegaSIM
- Dual Trust-Anchor Architecture using (U)SIM and MTM (mobile trusted module)
- Single Trust-Anchor Architecture using virtual SIMs and a MTM
Next he gives an introduction to the Trusted Computing Group's Mobile Phone Working Group (https://www.trustedcomputinggroup.org/groups/mobile).
Then he describes his work about virtual SIM cards that are based on a MTM.
-> OpenMTM http://sourceforge.net/projects/openmtm/
EMSCB Turaya http://www.emscb.com/
SIM and USIM Application Toolkit
Talk by Mr. Harald Summer from Giesecke & Devrient.
Mr. Summer explains the file system of the SIM. He shows a tool by G&D to view the file system. Next he shows the internals of a SAT application and explains what bytes flow from where to where. Hard core tech talk.
Enabling Trusted Mobile Applications with the SIM
Talk by Mrs. Stephanie Manning from Vodafone Group R&D. The focus of the talk is about how to integrate NFC and mobile phone technology. She describes her projects and the techonological challenges. Applications/Products are to be expected in the first half of 2008... They are using Global Platform 2.2 for their projects. Vodafone and Deutsche Bahn will have a trial this year: http://www.touchandtravel.de/. Mrs Manning does not expect that Vodafone will deploy applications to the phone's SIM because then application providers would have to have contracts with every mobile operator. Trusted Services Providers will take the role of deployer of applications to "rented" space on the (U)SIM.
Multi-application security platform UICC
Talk by Mrs. Chen Hao from Giesecke & Devrient GmbH.
Mrs. Chen Hao talks about the single wire protocol and the new developments in UICC technology in general. A further example of these new technologies is the definition of a USB 2.0 interface directly to the UICC. This will allow for having gigabytes of memory on the UICC.
Posted by
Unknown
at
10:13 AM
0
comments
![]()
Thursday, September 13, 2007
openinfocard id selector for Firefox signature validated
Finally! The signatures generated by the openinfocard id selector and the openinfocard STS are now accepted at relying parties that are based on Microsoft code. Mark Oluper from Microsoft's CardSpace team put the generated SAML assertions under his microscope and found the offending byte.
Axel,
The issue is that the key length doesn't match the signature length. The Windows CryptVerifySignature API verifies that the key length in bytes matches the signature length in bytes.
If you look at the modulus value for the Firefox identity selector generated assertion you will note that the value does not have the base 64 padding character whereas the signature value does. This results in a key length of 1032 bits (129 bytes) whereas the signature value is 1024 bits (128 bytes).
For the CardSpace generated assertion both the key length and signature length are equal to 2048 bits (256 bytes).
Regards,
Mark
So, what is the reason for this extra byte and why are the signatures accepted by relying parties that are Java based? Well, Java's BigInteger class introduces an extra null byte as the first byte when it converts a BigInteger into a byte array. I removed this extra null byte before base64 encoding the modulus of the signature key and now it works! AND the Java signature validation still works too!
Why does it work? Because Java just decodes the base64 encoded modulus and the constructor of BigInteger ignores extra null bytes but does not require them. There could be hundrets of null bytes and Java would still construct the same BigInteger modulus.
I did a quick check with self-issued and managed cards at several relying parties and all looks good.
- openinfocard RP (Java): local installation
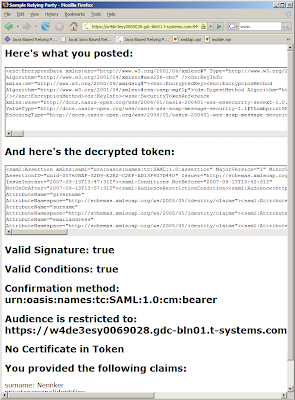
- Bandit Project RP: https://wag.bandit-project.org/BanditIdP/index.jsp

- jinformationcard demo shop (Java): https://zeno.fokus.fraunhofer.de/MiniShop/home.jsp

- FuGen Solutions' Demo RP: Microsoft Code https://socialphotos.federationportal.com/

- FriendsWithCards RP: Microsoft Code https://www.cardspacedemos.com/FriendsWithCards/

The new - latest and greatest - version of the id selector is here in the openinfocard download area.
Thanks again to Mike Jones and Mark Oluper for helping with this issue!
Posted by
Unknown
at
3:25 PM
2
comments
![]()
Tuesday, September 11, 2007
Populate Attribute From Infocard
This is the real application for information cards. Using them for authentication purposes is fine, but the transportation of claims/attributes is the real thing.
The id selector used here was, of course, the xmldap id selector for Firefox in its latest version 0.9.7.200709111523. I used a self-issued card and a managed card from the current openinfocard STS. The RP used was the Bandit's project server for the next interoperathon (sorry, you have to login at OSIS to read this. Don't ask me why.) in Barcelona.
Posted by
Unknown
at
5:28 PM
0
comments
![]()
Labels: claims informationcard
Saturday, September 08, 2007
Thursday, September 06, 2007
OSIS Identification Required
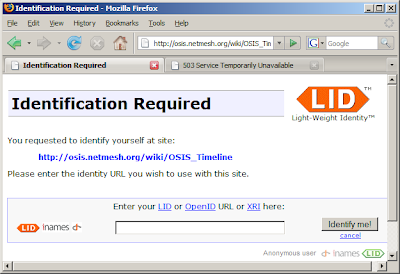
Why do I have to identify myself when I just want to view the new OSIS timeline?
What about "Minimal Disclosure for a Constrained Use"?! Or the German Bundesdatenschutzgesetzt §3: Datenvermeidung und Datensparsamkeit?
And then this:
I can not view the new OSIS timeline because my IdP is offline.
This should never happen ;-) /* my favorite comment in C programs */
But then you think "pseudonyms are cheap". Let's just choose another openid. BUT:
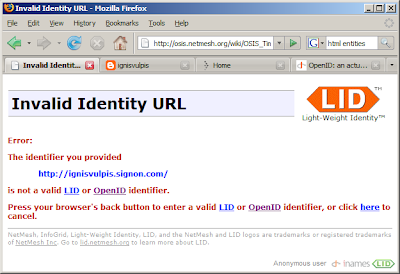
Signon.com tells me that this is my openid: ignisvulpis.signon.com
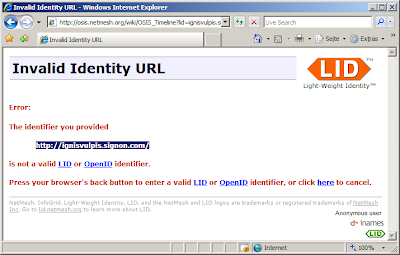
Just in case somebody thinks this might be Firefox specific or has anything to do with the xmldap id selector (0.9.6). It has not. Here is the IE7 result:
Stranded in the Metasystem.
Posted by
Unknown
at
8:56 AM
1 comments
![]()
Labels: OSIS PIP verisignlabs "laws of identity" xmldap "id selector"
Saturday, September 01, 2007
Openidcards
Thanks to Johnny Bufu's help I finally improved the xmldap Firefox id selector to be able to handle openidcards.
The id selector was retricted to SAML assertions as token type and could not handle "AppliesTo" correctly.
The new version can be downloaded here. Try it!
Again I want to thank Johnny for his patience and support. Without him I would not have found out about the wrong namespaces, missing elements etc. Thanks to Mike Jones too who did, as always, a great job bringing parties together.
Posted by
Unknown
at
9:20 AM
0
comments
![]()