TrustBearer and David Corcoran are doing cool stuff for years. Now they have been selected by Microsoft as one of two secure openid providers for HealthVault! 
Congratulations!
Interesting that Sean Nolan, chief architect of Microsoft’s HealthVault service, says that they are working to support Information Cards in HealthVault too!
Now let's put that on the patient's mobile phone.
Wednesday, June 25, 2008
Congratulations TrustBearer
Posted by
Unknown
at
2:58 PM
0
comments
![]()
Labels: healthvault, OpenId, trustbearer
Can People Learn?
It appears that the official identity data of many Germans was online readable for over three month... including religion and sometimes a photo.
How did this happen? Well, a software company that had successfully sold its eGovernment software to many German communities published the username and password of a demo version of their software on the internet. BUT this username and password happened to be the preinstalled standard username and password of the real application too. Ouch!
You don't need much fantasy to guess what some of the administrators of the sold software had failed to do...
I don't blame the administrators alone. Sure they probably violated the security policy of their organization but the bad security design of the application takes at least a quarter of the blame. Wait, let's put some blame on the German electronic signature laws too. The system of electronic signatures is so secure and expensive that nobody is willing to pay the price in Euros for it; not even or especially not the community and the government that made the laws.
This would not have happened had they used Information Cards.
Well, on the other hand it is not so complicated to use Information Cards in a way that is really stupid e.g. let anybody access the sensible data who presents a security token with the claim emailaddress == geheim@city.bund.de.
Posted by
Unknown
at
12:11 AM
0
comments
![]()
Labels: eGovernment, electronic signature, Information Cards
Tuesday, June 24, 2008
Information Card Foundation

The Information Card Foundation was officially launched today. Great.
The first press articles are on CNET and in the New York Times. I don't like the NYT's analogy of an "online ID card" that much... Information Cards let the user choose which ID she wants to use and from which identity provider it should be asserted. The ID might even be self-issued. There is no government asserted ID required.
---- Here follows the press release text -----
FOR IMMEDIATE RELEASE
TECHNOLOGY COMMUNITY FORMS INFORMATION CARD FOUNDATION TO SIMPLIFY SECURE ON-LINE DIGITAL IDENTITY
June 24, 2008 – Australia, Canada, France, Germany, India, Sri Lanka, United Kingdom, United States – An array of prominent names in the high-technology community today announced the formation of a non-profit foundation, The Information Card Foundation, to advance a simpler, more secure and more open digital identity on the Internet, increasing user control over their personal information while enabling mutually beneficial digital relationships between people and businesses.
Led by Equifax, Google, Microsoft, Novell, Oracle, and PayPal, plus nine leaders in the technology community, the group established the Information Card Foundation (ICF) to promote the rapid build-out and adoption of Internet-enabled digital identities using Information Cards.
Information Cards take a familiar off-line consumer behavior – using a card to prove identity and provide information – and bring it to the online world. Information Cards are a visual representation of a personal digital identity which can be shared with online entities. Consumers are able to manage the information in their cards, have multiple cards with different levels of detail, and easily select the card they want to use for any given interaction.
“Rather than logging into web sites with usernames and passwords, Information Cards let people ‘click-in’ using a secure digital identity that carries only the specific information needed to enable a transaction,” said Charles Andres, executive director for the Information Card Foundation. “Additionally, businesses will enjoy lower fraud rates, higher affinity with customers, lower risk, and more timely information about their customers and business partners.”
The founding members of the Information Card Foundation represent a wide range of technology, data, and consumer companies. Equifax, Google, Microsoft, Novell, Oracle, and PayPal, are founding members of the Information Card Foundation Board of Directors. Individuals also serving on the board include ICF Chairman Paul Trevithick of Parity, Patrick Harding of Ping Identity, Mary Ruddy of Meristic, Ben Laurie, Andrew Hodgkinson of Novell, Drummond Reed, Pamela Dingle of the Pamela Project, Axel Nennker, and Kim Cameron of Microsoft.
“The creation of the ICF is a welcome development,” said Jamie Lewis, CEO and research chair of Burton Group. “As a third party, the ICF can drive the development of Information Card specifications that are independent of vendor implementations. It can also drive vendor-independent branding that advertises compliance with the specifications, and the behind-the-scenes work that real interoperability requires.”
The Information Card Foundation will support and guide industry efforts to enable the development of an open, trusted and interoperable identity layer for the Internet that maximizes control over personal information by individuals. To do so, the Information Card infrastructure will use existing and emerging data exchange and security protocols, standards and software components.
Businesses and organizations that supply or consume personal information will benefit from joining the Information Card Foundation to improve their trusted relationships with their users. This includes financial institutions, retailers, educational and government institutions, healthcare providers, retail providers, travel, entertainment, and social networks.
The Information Card Foundation will hold interoperability events to improve consistency on the web for people using and managing their Information Cards. The ICF will also promote consistent industry branding that represents interoperability of Information Cards and related components, and will promote identity policies that protect user information. This branding and policy development is designed to give all Internet users confidence that they can exert greater control over personal information released to specific trusted providers through the use of Information Cards.
"Liberty Alliance salutes the open industry oversight of Information Card interoperability that the formation of ICF signifies," said Brett McDowell, executive director, Liberty Alliance. "Our shared goal is to deliver a ubiquitous, interoperable, privacy-respecting federated identity layer as a means to seamless, secure online transactions over network infrastructure. We look forward to exploring with ICF the expansion of the Liberty Alliance Interoperable(tm) testing program to include Information Card interoperability as well as utilization of the Identity Assurance Framework across Information Card deployments."
As part of its affiliations with other organizations, The Information Card Foundation has applied to be a working group of Identity Commons, a community-driven organization promoting the creation of an open identity layer for the Internet while encouraging the development of healthy, interoperable communities.
Additional founding members are Arcot Systems, Aristotle, A.T.E. Software, BackgroundChecks.com, CORISECIO, FuGen Solutions, the Fraunhofer Institute, Fun Communications, the Liberty Alliance, Gemalto, IDology, IPcommerce, ooTao, Parity, Ping Identity, Privo, Wave Systems, and WSO2.
Further information about the Information Card Foundation can be found at www.informationcard.net.
Media Contact:
work+1-781-223-5833
johnfitzsimmons4@hotmail.com
Posted by
Unknown
at
11:52 AM
2
comments
![]()
Labels: Information Card Foundation
Sunday, June 22, 2008
The Seven Laws Wordle

Wordling things (texts) seems to be á la mode. I could not resist to wordle Kim Cameron's Seven Laws of Identity....
Posted by
Unknown
at
11:31 PM
0
comments
![]()
Labels: identity, Kim Cameron, The Laws of Identity, wordle
Thursday, June 19, 2008
Information Card Size

Having Information Cards stored on limited capability devices (USB Tokens, SIM cards, UICC cards etc) currently is a difficult because many of the more secure devices have very little memory. People who have openend a crd file with an text editor or looked at a card in RoamingInformationCard format might have noticed that most of the space needed is due to the card image.
I suggest that we change the Information Card format and introduce a new element that is a reference to the actual image.
Instead of:
<ic:InformationCard xml:lang="xs:language" ...>
<ic:InformationCardReference> ... </ic:InformationCardReference>
<ic:CardName> xs:string </ic:CardName> ?
<ic:CardImage MimeType=”xs:string”> xs:base64Binary </ic:CardImage> ?
<ic:Issuer> xs:anyURI </ic:Issuer>
<ic:TimeIssued> xs:dateTime </ic:TimeIssued>
<ic:TimeExpires> xs:dateTime </ic:TimeExpires> ?
<ic:TokenServiceList> ... </ic:TokenServiceList>
<ic:SupportedTokenTypeList> ... </ic:SupportedTokenTypeList>
<ic:SupportedClaimTypeList> ... </ic:SupportedClaimTypeList>
<ic:RequireAppliesTo ...> ... </ic:RequireAppliesTo> ?
<ic:PrivacyNotice ...> ... </ic:PrivacyNotice> ? ...
</ic:InformationCard>
I would like to have something like:
<ic:InformationCard xml:lang="xs:language" ...>
<ic:InformationCardReference> ... </ic:InformationCardReference>
<ic:CardName> xs:string </ic:CardName> ?
<ic:CardImageRef MimeType=”xs:string”
hash="xs:base64Binary"
width="xs:unsignedInt"px height="xs:unsignedInt"px filesize="xs:unsignedInt"
href="xs:anyURI"/> ?
<ic:Issuer> xs:anyURI </ic:Issuer>
<ic:TimeIssued> xs:dateTime </ic:TimeIssued>
<ic:TimeExpires> xs:dateTime </ic:TimeExpires> ?
<ic:TokenServiceList> ... </ic:TokenServiceList>
<ic:SupportedTokenTypeList> ... </ic:SupportedTokenTypeList>
<ic:SupportedClaimTypeList> ... </ic:SupportedClaimTypeList>
<ic:RequireAppliesTo ...> ... </ic:RequireAppliesTo> ?
<ic:PrivacyNotice ...> ... </ic:PrivacyNotice> ? ...
</ic:InformationCard>
- hash="xs:base64Binary"
The SHA-1 hash of the image data - width="xs:unsignedInt"px height="xs:unsignedInt"px filesize="xs:unsignedInt"
The width and height of the image in pixel and/or filesize in bytes (optional) - href="xs:anyURI"
The URL where the image data can be retrieved
The id selector can now choose the "right" image for the mobile device based on the image size, but more importantly it can now cache images in the case when more then one card has the same image (URL and hash) or the image was downloaded before. The hash is a protection against DNS spoofing. Alternatively we could define that the href must use SSL and use the id selectors certificate based protection mechanisms against attacks.
Posted by
Unknown
at
2:19 PM
0
comments
![]()
Labels: information card, information card image
Thursday, June 12, 2008
Instant Install of Managed Card
I changed the openinfocard id selector and the xmldap idp to make it easier to install managed cards.
Let's say you visit the IdP of your trust and have logged into its service using username and password. In fact the choice of this authentication might influence the rest of this scenario.
After authentication you are presented the list of your current cards:
Formerly you were presented with a list of links that you could click and you had to save the .crd file to disk, then open the id selector of your choice to import the card.
Now, you have noticed the column of little icons, you can invoke the id selector directly. Let's say use click on one of these icons (20071018xmldap):
The new card wizard of the openinfocard id selector has opened and the card is retrieved from the URL that was delivered to the id selector.
After this you are (currently) back to the page that shows the list of your cards and you might now open the id selector to verify that the new card was imported (20071018xmldap):
Well, how does this work?! I use a special tokentype "urn:oasis:names:tc:IC:1.0:managedcard" that tells the openinfocard id selector to use the value of the "issuer" parameter to retrieve and import the card.
There might be better ways to do it and there is a precondition here that I did not mention. Do you see it?
Back to the IdP authentication... Instead of username and password an IdP might have allowed authentication with a self-issued card and then that card could be used for authentication when the managed card is used to provide claims to a relying party!
(More preconditions here... Find them!!! and discuss this either here on this blog or here)
Posted by
Unknown
at
9:34 AM
0
comments
![]()
Wednesday, June 11, 2008
OASIS event
Topics include, but are not limited to:
- High-level overviews of security challenges, and the landscape of security standards being developed to address them
- Case studies, requirements, deployment overviews, profiles from specific sectors or application areas (e-governments, telecom, financial services, healthcare...)
- Authentication of citizens in cross-border government services, issues related to mutual recognition of authentication services
- Information cards and information card interoperability
- Federated technologies
- Access control, access control models, policies, and privacy issues
- Key management (PKI or symmetric key-based)
- Digital Signatures, electronic signatures, server-based signature processing, technical and legal issues.
- Securing Web Services: WS-I profiles; recent Web Services security specifications
This happens together with the workshop "Adopting SOA for Telecom".
Sounds interesting, I would like to attend. Gerry Gebel is giving the keynote and Anthony Nadalindrsecure@us.ibm.com is on the workshop committee.
Posted by
Unknown
at
10:53 AM
0
comments
![]()
Labels: event, federation, information card, OASIS, telco
Thursday, June 05, 2008
Information Card (?) Icon Mania
I am missing a gene that makes that I don't understand usage guidelines and IPR discussions.
Posted by
Unknown
at
3:42 PM
1 comments
![]()
Labels: information card, information card icon
Doppelgänger
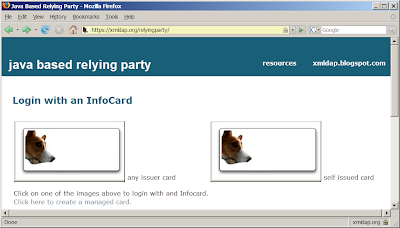
Today I updated the xmldap relyingparty to contain two HTML objects of type "application/x-informationcard". To keep things simple I just have put two forms on the website each containing one object. The only difference between the two is that on requires a self-issued card while the other does not restrict the issuer.
The id selectors seem to handle this well. I tested it with the openinfocard id selector and with CardSpace.
What is this good for?! Well, one object could request a card from the issuer "Mastercard" while the other requests a card from the issuer "Visa". Or one could request an issuerpolicy while the other does not...
Interestingly CardSpace fails the test on Pamela's test page for the OSIS interop test. It seems that CardSpace does not like the missing "requiredclaims" parameter...
The openinfocard id selector has its flaws too but they don't stop this test from "working" or do they?
Posted by
Unknown
at
3:08 PM
0
comments
![]()
Labels: CardSpace, openinfocard, osis, xmldap
Tuesday, June 03, 2008
OSIS I3 Information Card RelyingParty Feature Test
The sad truth is that nobody really cared to fill out the feature test tables for relyingparties during the OSIS I3 interop. This table shows only relyingparties that have at least one test result other than "Not Tested". The xmldap RP and all Microsoft RPs were deleted from the table for this reason. Even features that most RPs support have no utilizable value. The last two rows of the table should show "Works" for probably all RPs but they show the dreaded "Not Tested"...
This table is not usefull to conclude the maturity of the Identity Metasystem from it. Shame on us. Shame on me.
Posted by
Unknown
at
3:26 PM
2
comments
![]()
Monday, June 02, 2008
Microformatified
Today I began to put Microformats in my blog and installed the operator extension into Firefox to see and work with microformats. I was astonished that blogger has put a little bit of microformat into my blog already. Using operator or a similar tool you can now work on the tags, export events and contact information. This is a nice start. Next I want services specifications; either XRDS (simple) or Microsoft's openservices?!
Please notice the green cross and the new "operator" toolbar.
Posted by
Unknown
at
2:42 PM
0
comments
![]()
Labels: link, microformat, xrds